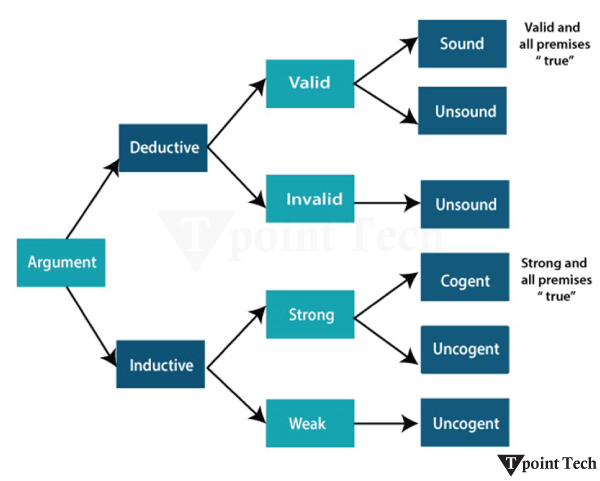
Till now, we have learned knowledge representation using first-order logic and propositional logic with certainty, which means we were sure about the predicates. With this knowledge representation, we might write A→B, which means if A is true, then B is true, but consider a situation where we are not sure about whether A is true or not, then we cannot express this statement; this situation is called uncertainty.
So, to represent uncertain knowledge, where we are not sure about the predicates, we need uncertain reasoning or probabilistic reasoning.
Causes of Uncertainty
The following are some leading causes of uncertainty to occur in the real world.
- Information occurred from unreliable sources.
- Experimental Errors
- Equipment fault
- Temperature variation
- Climate change
Understanding Probabilistic Reasoning
Probabilistic reasoning is a way of knowledge representation where we apply the concept of probability to indicate the uncertainty in knowledge. In probabilistic reasoning, we combine probability theory with logic to handle uncertainty.
We use probability in probabilistic reasoning because it provides a way to handle the uncertainty that is the result of someone’s laziness and ignorance.
In the real world, there are lots of scenarios where the certainty of something is not confirmed, such as “It will rain today,” “the behavior of someone in some situations,” or “A match between two teams or two players.” These are probable sentences for which we can assume that it will happen, but we are not sure about it, so here we use probabilistic reasoning.
Need for probabilistic reasoning in AI:
- When there are unpredictable outcomes.
- When specifications or possibilities of predicates become too large to handle.
- When an unknown error occurs during an experiment.
In probabilistic reasoning, there are two ways to solve problems with uncertain knowledge:
- Bayes’ rule
- Bayesian Statistics
Note: We will learn the above two rules in later chapters.
As probabilistic reasoning uses probability and related terms, before understanding probabilistic reasoning, let’s know some common terms:
Probability: Probability can be defined as the chance that an uncertain event will occur. It is the numerical measure of the likelihood that an event will occur. The value of probability always remains between 0 and 1, which represents ideal uncertainties.
- 0 ≤ P(A) ≤ 1, where P(A) is the probability of an event A.
- P(A) = 0 indicates total uncertainty in event A.
- P(A) =1 indicates total certainty in event A.
We can find the probability of an uncertain event by using the following formula.

- P(¬A) = probability of an event not happening.
- P(¬A) + P(A) = 1.
- Event: Each possible outcome of a variable is called an event.
- Sample Space: The collection of all possible events is called the sample space.
- Random Variables: Random variables are used to represent the events and objects in the real world.
- Prior Probability: The prior probability of an event is the probability computed before observing new information.
- Posterior Probability: The probability that is calculated after all evidence or information has been considered. It is a combination of prior probability and new information.
Conditional probability:
Conditional probability is the probability of an event occurring when another event has already happened.
Let’s suppose we want to calculate event A when event B has already occurred, “the probability of A under the conditions of B” can be written as:

Where,
P(A⋀B)= Joint probability of A and B
P(B)= Marginal probability of B.
If the probability of A is given and we need to find the probability of B, then it will be given as:

It can be explained by using the below Venn diagram, where B is the occurrence of an event, so the sample space will be reduced to set B, and now we can only calculate event A when event B has already occurred by dividing the probability of P(A⋀B) by P( B ).

Example:
In a class, there are 70% of the students like English and 40% of the students like English and mathematics. What is the percentage of students who like English and also like mathematics?
Solution:
Let A be an event that a student likes Mathematics
B is an event where a student likes English.

Hence, 57% are students who like English and Mathematics.
Probabilistic Models in AI
In the essence of artificial intelligence, the probabilistic models can help the efficient administration of uncertainty and can assist in depicting complex relations between variables.
Bayesian Networks
Belief networks, Bayesian Networks, are a more common name and show probabilistic dependencies among variables in the form of a graphical structure. They are composed of:
- Nodes: Every node in the Bayesian network is equivalent to a random variable, which could be another variable or continuous.
- Edges: Edges going from one node to another represent that a variable at the starting node affects the conditional probability of the variable at the end node.
- Conditional Probability Tables (CPTs): Each node contains a CPT that indicates the degree of dependence of the node in relation to the variables presented by its parent nodes.
For illustration, in a medical diagnosis network, an individual variable, such as “Fever”, might depend on “Infection”, denoted by arrows between the nodes and a CPT, special probability values.
Markov Models
Markov Chains
It is a probabilistic model used in modelling systems that evolve via state changes. Key characteristics include:
- Memoryless Property: The following state is dependent on the present state and not the one before it.
- State Transition Matrix: Shows opportunities for changing from one state to another.
A weather model may attempt to display changes in weather through its “Sunny,” “Cloudy”, and “Rainy” states.
Hidden Markov Models (HMM)
HMMS is based on Markov Chains but adds hidden (latent) states:
- Observed States: Outputs generated by the system.
- Hidden States: Factors that are undetected to let us observe something.
- Emission Probabilities: The Possibility of observing particular states with hidden elements.
Dynamic Bayesian Networks (DBNs)
Dynamic Bayesian Networks generalise the Bayesian Networks setting to be able to follow evolving processes that extend over many time steps. They illustrate how variables act over time, including both static and dynamic connections.
- Temporal Dependencies: Demonstrate the way that variables change from one time step to another.
- Transition Models: Describe the chance of being in a different state in the long run.
Applications of Probabilistic Reasoning
Natural Language Processing (NLP)
- Language Modelling: N-grams and neural probabilistic language models come under modelling systems based on probability, which judge a sequence of words determined by probability and to which text generation and autocomplete features owe their development.
- Speech Recognition: The process of empowering spoken language alignment with HMMs and probabilistic algorithms increases the quality of transcriptions because of higher accuracy.
- Machine Translation: A variety of statistical machine translation systems take advantage of the employment of probabilistic algorithms, providing both good and poor-mode translations as they relate to their contextual meaning.
- Sentiment Analysis: Bayesian approaches calculate the probabilities of certain sentiments being presented in a text, improving opinion analysis and sentiment classification.
Robotics and Autonomous Systems
- Localisation and Mapping: Techniques, such as Monte Carlo Localisation and SLAM, allow robots to localise and map their environment for easy navigation.
- Path Planning: Robots that calculate the probability of a danger-free condition of specific routes can move safely.
- Decision-Making under Uncertainty: Robots are equipped with Bayesian networks and MDPs to handle uncertain data and respond appropriately, hence appropriate for situations with insufficient or noisy information.
- Human-Robot Interaction: Probabilistic models allow robots to recognise human intentions, and this increases their cooperation and communication.
Medical Diagnosis and Decision Support
- Disease Diagnosis: Based on processing symptoms and test results, Bayesian networks establish the probabilities of occurrence for specific diseases, facilitating good diagnosis calls by medical personnel.
- Predictive Analytics: Information processed using probabilistic models assists healthcare providers in predicting how a disease will develop and where preventive measures will be required.
- Treatment Recommendation Systems: Algorithms analyse the medical history of a patient, genetic details, and previous responses to treatments to personalise therapy recommendations.
- Clinical Decision Support: Machine-based systems utilise probabilistic analysis to recommend diagnostic checks and interpret their results.
Recommender Systems
- Collaborative Filtering: Probabilistic models analyse user interactions, identifying repeating patterns, and suggest items that match similar user behaviours.
- Content-Based Recommendations: Applying Bayesian techniques, with the help of characteristics and their historical interactions, the probability of a user liking an item by a user is known.
- Hybrid Approaches: More accurate recommendations can be achieved from a combination of synergised probabilistic, collaborative, and content-based methods.
- Dynamic Preferences: When users change their preferences, algorithms adjust their recommendations based on the application of probabilistic temporal models.
Fraud Detection
- Anomaly Detection: Bayesian and probabilistic methods estimate the anomalies for transactions and indicate signs of possible fraud.
- Risk Scoring: Fraud detection systems judge if a transaction is fraudulent by using previous data and situational information.
- Network Analysis: Probabilistic graph models reveal hidden connections and activities characteristic of fraud in financial or social networks.
- Real-Time Decision-Making: Instant algorithms judge while risking further racist behaviour or financial ruin.
Despite the effectiveness of probabilistic reasoning in the management of uncertainty in decision-making, it is prone to be hampered by practical issues undermining its successful implementation. Addressing these issues is a prerequisite for enlarging the application of probabilistic reasoning in artificial intelligence.
Challenges in Probabilistic Reasoning
Scalability Issues
The more complex the AI system is, the more problematic the task of probabilistic models to deal with data and calculations will be.
- Large-Scale Networks: The manipulation of such many variables and dependencies that Bayesian networks and their counterparts require compels a great deal of computational power. As an example, the complexities of weather or financial markets require handling enormous data sets to make a correct model design.
- High-Dimensional Data: The more variables that are added, the more one gets into a condition where probability distributions are exponentially increased, thus effectively depicting the “curse of dimensionality”.
- Real-Time Applications: In practical situations such as self-driving cars and the recommendation of websites, there is an urgent need for immediate and fast inference capabilities. Performance in finding a balance point between speed and accuracy continues to pose two great challenges to probabilistic reasoning models in such applications.
- Potential Solutions: To solve these problems, new algorithms like variational inference, parallel computation, and frameworks such as TensorFlow Probability are employed.
Computational Complexity
Probabilistic reasoning models have their share of beautiful computations that may soon necessitate large amounts of processing.
- Exact Inference: Techniques such as variable elimination and belief propagation have exponential complexities under conditions that restrict their applicability to large-scale systems.
- Sampling Methods: Such techniques (Monte Carlo and Gibbs Sampling) can be computationally expensive (and require a lot of computational capacity) if a high degree of precision is needed.
- Dynamic Systems: Integrating the time-varying dynamics into Bayesian networks, where dynamic models are used, places additional computational demands, requiring the iterative application of state transition updates.
- Potential Solutions: Using hybrid algorithms that combine both deterministic and probabilistic methods and using GPU and TPU technology, computational inefficiencies can be overcome.
Data Sparsity and Quality
The probability model’s accuracy largely depends on the availability of high-quality and large data. Poor or thin data may produce unreliable inferences and wrong predictions.
- Sparse Data: Routine acquisition of complete and reliable data samples for the successful testing of probabilities can be quite problematic. It is generally difficult to model complex events such as system outages or catastrophic weather events because they are poorly reflected in the data sets.
- Noisy Data: Unhandled or noisier datasets can easily lead to biased outcomes and compromise the validity of inferences. This problem is particularly critical in such areas as medical diagnostics, in which mistakes in data interpretation can cause severe health risks.
- Imbalanced Data: When this data is not balanced among the various categories, probabilistic methods may generate biased predictions.
- Potential Solutions: As a solution for data sparsity and maintaining the quality of the data, practitioners regularly implement techniques such as data augmentation, transfer learning, and reliable statistical estimation strategies. Subject matter experts’ insights can substantially enhance probabilistic models when the coverage of the dataset is limited.
Tools and Frameworks for Probabilistic Reasoning in Artificial Intelligence
Underlying Artificial Intelligence (AI), there lies probabilistic reasoning, and there are a lot of specialised techniques and frameworks that are available to promote its use. With these tools, the construction and implementation of probabilistic models with inbuilt inference, learning, and simulation features are simplified.
Pyro
Developed based on PyTorch, Pyro allows the developers of such models to instantly build and deploy probabilistic models that are scalable and flexible.
Key Features:
- Permits the Bayesian inference and stochastic processes.
- Simplifies the development of neural network-based probabilistic models by integrating with PyTorch.
- Provides support for both variational inference and Markov Chain Monte Carlo (MCMC) approaches.
- Enables the creation of customised probabilistic frameworks.
Use Cases:
- Complex hierarchical Bayesian models.
- Time-series forecasting using probabilistic approaches.
- Robust efficiencies in developing machine learning models that support scientific research and experimental techniques.
TensorFlow Probability (TFP)
TensorFlow Probability adds modules for probabilistic modelling and high-end statistical computation to the functionality of TensorFlow.
Key Features:
- Supports many distribution, densities, and transformation operations.
- Provides capabilities for Bayesian inference, Monte Carlo sampling, and optimisation techniques.
- Plugging into TensorFlow enables the generation of hybrid models based on the combination of deep learning with probabilistic methodologies.
- Automatic differentiation for gradient-based optimisation.
Use Cases:
- Creating combined deep learning and statistical models for use in applications like uncertainty quantification.
- Statistical modelling of financial and healthcare data analysis.
- Examining the possibility of optimising predictions via the use of Bayesian neural networks.
Pomegranate
Pomegranate is a probabilistic modelling library for Python, focused on simplicity and efficiency.
Key Features:
- The library provides implementations for many probabilistic models, such as Bayesian networks, Hidden Markov Models, and Gaussian Mixture Models.
- Provides speed increases by using Cython.
- The design is modular, and it makes one’s customisation easy, and experimenting with different approaches is easier.
- Allows Model parameter estimation even where data is missing.
Use Cases:
- An application of probabilistic models to sequential data in such areas as speech and transcription recognition and bioinformatics.
- Application of probabilistic algorithms for clustering and classification in unsupervised learning setups.
- Fast real-time probabilistic inference tailored to embedded systems and robotics.